|
Size: 6340
Comment:
|
← Revision 76 as of 2025-05-11 08:48:11 ⇥
Size: 8072
Comment:
|
| Deletions are marked like this. | Additions are marked like this. |
| Line 1: | Line 1: |
| = Keepass = | = KeePassXC = {{attachment:keepassx.png}} |
| Line 7: | Line 9: |
| == Features == * Different passwords for different accounts. * MFA for modern accounts/services- this becomes so easy, use it wherever it is possible. * No single device dependency. Your passwords are where you are. * Splitted security levels (multiple vaults). * Awesome browser integration. * Sharing credentials (multiple vaults, shared via cloud storage). E.g. a) team: sharing credentials, b) family: shared WLAN password, children school accounts. |
|
| Line 9: | Line 20: |
| !KeePass(X) is a tool to store and manage passwords. It is freely available for | KeePassXC is a tool to store and manage passwords. Apps are freely available for |
| Line 11: | Line 22: |
| * MacOS/Windows/Linux - !KeePass: https://keepassxc.org/. * Android: https://play.google.com/store/apps/details?id=com.kunzisoft.keepass.free |
* MacOS/Windows/Linux - KeePassXC: https://keepassxc.org/. * Android: [[https://play.google.com/store/apps/details?id=com.kunzisoft.keepass.free|KeepassDX]] |
| Line 14: | Line 25: |
Mobile Integration: * We have tested KeePassXC on mobile devices only very roughly. * The integration is not as good ('simple to use') as on the desktop app or in the browser. * Never the less: most persons see's it as an advantage to have the personal vault on their mobile device accessible. |
|
| Line 17: | Line 35: |
| * KeePassXC create/open/edit/save password-databases in a single file. * A password-database is basically an encrypted file, where you can store your various usernames/passwords/URLs and also attachments like pictures or other important / private documents. * A password-database can only be opened if you know the Master-Password. The Master Password is the key to all your stored passwords. |
* KeePassXC create/open/edit/save password-vaults in a single file. * A password-vault is basically an encrypted file, where you can store your various usernames/passwords/URLs and also attachments like pictures or other important / private documents. * A password-vault can only be opened if you know the Master-Password. The Master Password is the key to all your stored passwords. |
| Line 21: | Line 39: |
| * Encryption -- either the Advanced Encryption Standard (AES) or the Twofish algorithm are used for encryption of the database in 256 bit sized increments | * Encryption -- either the Advanced Encryption Standard (AES) or the Twofish algorithm are used for encryption of the vault in 256 bit sized increments |
| Line 24: | Line 42: |
| == Using KeePassXC on the Thinlinc terminals == * Start KeePassXC: * Ubuntu / Thinlinc: Applications > Accessoires > KeePassXC * command line: keepassxc * You can use the same password database on different computers if they have KeePassXC installed. * When opening KeePassXC with a database, you will be asked for the master password of the file. * When a password database is open, KeePassXC "locks itself" after a certain amount of time. After that you have to unlock the file again with your master password. * You can hide/view usernames and passwords by clicking on "View" --> "Hide Usernames" and "View" --> "Hide Passwords" * You can right-click on an entry and choose "Copy Username to Clipboard" or "Copy Password to Clipboard". You can then paste the password. After a few seconds, the password is no longer stored in the Clipboard. == Creating a Password Database == |
== Creating a Password Vault == |
| Line 38: | Line 45: |
| * you will be prompted to set a master key. Input your master password (the master password for all your other stored passwords). Then click "OK" * repeat your master password. click "OK". * chose a group. (Standard choices are Internet of eMail. You can also create your own groups). * click on "Entries" --> "Add New Entry..." |
* You will be prompted to set a master key. Input your master password (the master password for all your other stored passwords). Then click "OK" * Repeat your master password. click "OK". * Chose a group. (Standard choices are Internet of eMail. You can also create your own groups). * Click on "Entries" --> "Add New Entry..." |
| Line 49: | Line 56: |
| * click on "File" --> "Save Database" * chose a location and a name for your password database. click "OK" |
* Click on "File" --> "Save Database" * Chose a location and a name for your password database. click "OK" |
| Line 52: | Line 59: |
| == Best practice: Sync Database via cloud == | == Best practice: Sync Vault via cloud == |
| Line 54: | Line 61: |
| * Only use a cloud service if you need to sync your passwords over several devices. | * Only use a cloud service if you need to sync your passwords across several devices! (Recommendation: yes, use a cloud service) |
| Line 59: | Line 66: |
| * creates automatically backups. | * implicit backups (data on multiple devices, and also in the cloud). |
| Line 62: | Line 69: |
| * If your cloud access is compromised or the cloud service provider is compromised: the thief owns the treasure. | * all of your confidental data on all devices - higher chance that your (encrypted) vaults are accessible to others. * If your cloud access is compromised or the cloud service provider is compromised: the thief owns the (enrypted) vault. |
| Line 72: | Line 80: |
| * https://drive.switch.ch - Switch Eduction cloud service - '''switchdrive''' * [[drive.math.uzh.ch]] - I-MATH |
* [[https://drive.switch.ch]] - Switch Eduction cloud service - '''switchdrive''' * [[https://drive.math.uzh.ch]] - I-MATH |
| Line 77: | Line 85: |
| * On all devices where you like to sync your !KeePass database file, install and configure [[drive.math.uzh.ch]] * Open the !KeePass database file on all of your devices directly from the cloud folder. |
* On all devices where you like to sync your KeePassXC Vault file, install and configure [[drive.math.uzh.ch]] * Open the KeePassXC vault file on all of your devices directly from the cloud folder. * Automatic merge of vault: Even if KeePassXC has a vault opened, changes on a different device (e.g. phone) and sync via cloud, becomes immediately active. * If you work in a team: no change, everyone can open the local copy - changes will be merged. |
| Line 82: | Line 94: |
| * KeepassXC can be used from within a browser (Chrome, Chromium, Firefox, Vivaldi, Brave, ...) * Browser connection to KeepassXC is nice: different browsers offer the same accounts/credentials - if synced via cloud than also on different computers. |
* KeePassXC can be used from within a browser (Chrome, Chromium, Firefox, Vivaldi, Brave, ...) * Browser connection to KeePassXC is nice: different browsers offer the same accounts/credentials - if synced via cloud than also on different computers. |
| Line 86: | Line 98: |
| * Again, think on this: There is only one source of truth (=one KeePassXC vault), in all browsers you have all your credentials available. | |
| Line 87: | Line 100: |
| Finally: no more MS-Authenticator app needed, no more single device dependency, login to any MFA protected website without a mobile phone. | Finally: * '''no more MS-Authenticator app needed''' * '''no more single device dependency''' (Phone at home, ...) * '''login to any MFA protected website without a mobile phone''' - Biggest advantage: your second token are controlled by you, not any provider. * '''still secure''' - the second factor is now your KeePassXC. |
| Line 100: | Line 118: |
| attachment:kp-passskeys.png | {{attachment:kp-passskeys.png}} |
| Line 104: | Line 122: |
| * Take care that the keepass icon on the top right is 'green' = connection to database is active. | * Take care that the KeePassXC icon on the top right is 'green' = connection to vault is active. |
| Line 116: | Line 134: |
| * To use TOTP with Microsoft Office 365 login: [[MFA/Microsoft_Authentication#Add_third_party_TOTP_app|Third Party]] | * To use TOTP with Microsoft Office 365 login: Add another (than MS-Authenticator-) app, as second factor [[MFA/Microsoft_Authentication#Add_third_party_TOTP_app|How To]] |
| Line 120: | Line 138: |
| * On a MFA-TOTP secured login website, just login as usual with keepass, on the next page, where the one time token is requested, click again on the green symbol. | * On a MFA-TOTP secured login website, just login as usual with KeePassXC, on the next page, where the one time token is requested, click again on the green symbol. |
| Line 128: | Line 146: |
| * Or as a QR code to scan. Here sometimes it's a URL or a `fido` string. If it is not in plaintext in the URL, hopefully the assigned app (=keepassdx) opens. | * As a QR code to scan. * Here sometimes it's a URL or a `fido` string. * If it is not in plaintext in the URL, hopefully the assigned app (=keepassdx) opens. * Option: be creative - scan the QR, look at the url (or send the URL via 'share' to yourself): you should see the shared secret as an argument in the URL. |
| Line 133: | Line 155: |
| * Some websites work better than others. | |
| Line 135: | Line 156: |
| * But: Some websites work better than others. E.g. eduid.ch is ok, gitlab is ok but with popup, Microsoft is broken for Linux/Chrome/KeePassXC, ... === Recovery Keys === * Some services offers recovery keys. * Copy the keys in corresponding account record in KeePassXC. * If you used a key (it's burnt now), remove it from the list (if there was only one key, update it with the new one). == Same account / different URLs == * Some services, especially Microsoft (https://login.live.com/, https://login.microsoftonline.com/), uses different URLs to login. * Per account, add further URLs: {{attachment:kp-addurl.png}} * This is very '''powerful''' - add as many URLs you like to the same account record - the helps to keep your vault clean! |
KeePassXC
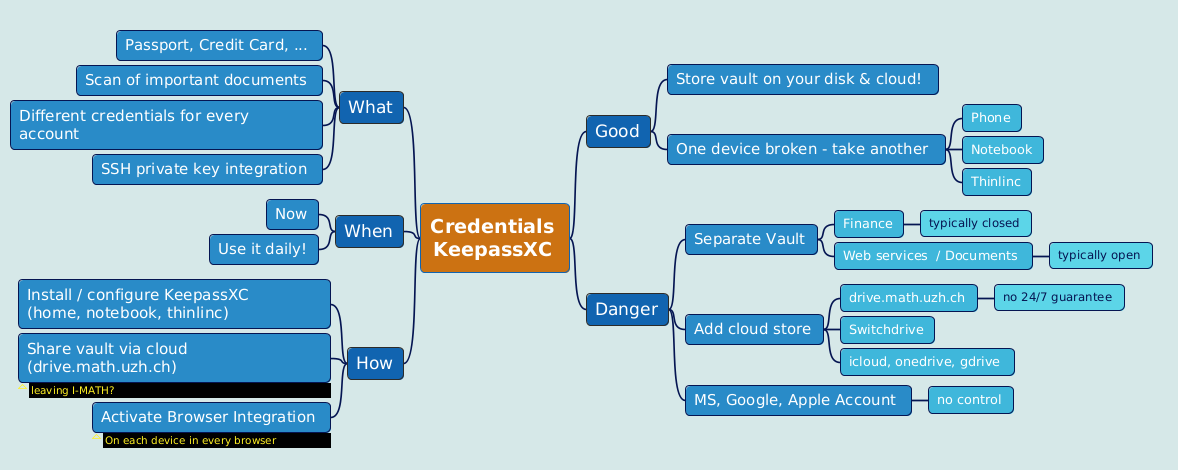
Contents
Background information: https://www.heise.de/news/Open-Source-Adventskalender-Der-Passwort-Manager-KeePass-6288780.html
Features
- Different passwords for different accounts.
- MFA for modern accounts/services- this becomes so easy, use it wherever it is possible.
- No single device dependency. Your passwords are where you are.
- Splitted security levels (multiple vaults).
- Awesome browser integration.
- Sharing credentials (multiple vaults, shared via cloud storage). E.g. a) team: sharing credentials, b) family: shared WLAN password, children school accounts.
Description
KeePassXC is a tool to store and manage passwords. Apps are freely available for
MacOS/Windows/Linux - KeePassXC: https://keepassxc.org/.
Android: KeepassDX
iOS - https://keepassium.com/
Mobile Integration:
- We have tested KeePassXC on mobile devices only very roughly.
- The integration is not as good ('simple to use') as on the desktop app or in the browser.
- Never the less: most persons see's it as an advantage to have the personal vault on their mobile device accessible.
How KeePassXC works
- KeePassXC create/open/edit/save password-vaults in a single file.
- A password-vault is basically an encrypted file, where you can store your various usernames/passwords/URLs and also attachments like pictures or other important / private documents.
- A password-vault can only be opened if you know the Master-Password. The Master Password is the key to all your stored passwords.
- If you forgot your Master-Password, you cannot access your stored passwords anymore.
- Encryption -- either the Advanced Encryption Standard (AES) or the Twofish algorithm are used for encryption of the vault in 256 bit sized increments
All features: http://www.keepassx.org/features/
Creating a Password Vault
Click on "File" --> "New Database..."
- You will be prompted to set a master key. Input your master password (the master password for all your other stored passwords). Then click "OK"
- Repeat your master password. click "OK".
- Chose a group. (Standard choices are Internet of eMail. You can also create your own groups).
Click on "Entries" --> "Add New Entry..."
- Input the information you need
- Title: a short description of the entry
- Username: your username
- URL: on what homepage do you need the password
- Password: your password
- Repeat: repeat your password
- Comment: a longer description of the entry
Click on "File" --> "Save Database"
- Chose a location and a name for your password database. click "OK"
Best practice: Sync Vault via cloud
- Only use a cloud service if you need to sync your passwords across several devices! (Recommendation: yes, use a cloud service)
- Decide on your own:
- Pro 'cloud':
- all of your confidental data on all devices.
- implicit backups (data on multiple devices, and also in the cloud).
- Contra 'cloud':
- all of your confidental data on all devices - higher chance that your (encrypted) vaults are accessible to others.
- If your cloud access is compromised or the cloud service provider is compromised: the thief owns the (enrypted) vault.
- Pro 'cloud':
US based cloud provider like Google Drive, Dropbox, Apple iDrive, Microsoft OneDrive:
- Those services are very attractive to hackers.
- The NSA has the right to get all data from US companies. After Snowden it's for sure, the NSA is not friendly.
Rule of thumb: Don't use US hosted / company based services for confidential data.
- Local cloud storage provider:
https://drive.switch.ch - Switch Eduction cloud service - switchdrive
https://drive.math.uzh.ch - I-MATH
- How to:
On all devices where you like to sync your KeePassXC Vault file, install and configure drive.math.uzh.ch
- Open the KeePassXC vault file on all of your devices directly from the cloud folder.
- Automatic merge of vault: Even if KeePassXC has a vault opened, changes on a different device (e.g. phone) and sync via cloud, becomes immediately active.
- If you work in a team: no change, everyone can open the local copy - changes will be merged.
Browser integration / MFA Setup / Passkeys
- KeePassXC can be used from within a browser (Chrome, Chromium, Firefox, Vivaldi, Brave, ...)
- Browser connection to KeePassXC is nice: different browsers offer the same accounts/credentials - if synced via cloud than also on different computers.
- TOTP service (one time token).
- Passkeys support.
- Again, think on this: There is only one source of truth (=one KeePassXC vault), in all browsers you have all your credentials available.
Finally:
no more MS-Authenticator app needed
no more single device dependency (Phone at home, ...)
login to any MFA protected website without a mobile phone - Biggest advantage: your second token are controlled by you, not any provider.
still secure - the second factor is now your KeePassXC.
Settings
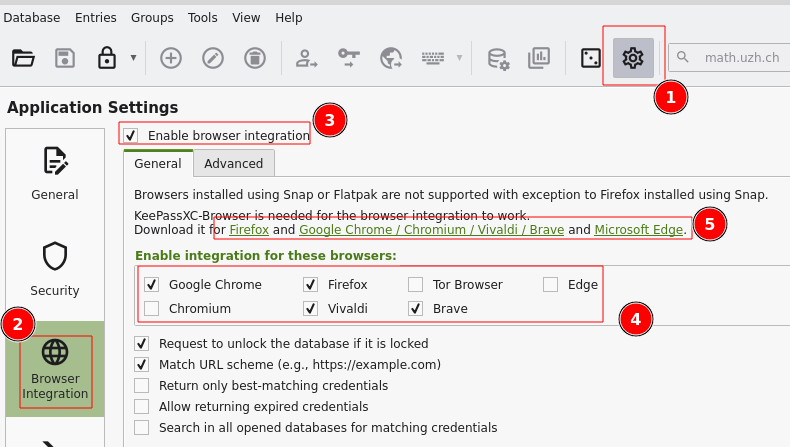
Settings > Browser Integration > Enable integration ...: Chrome, Firefox, ...
Browser Plugin
- Install the corresponding browser plugin (links to app store: check settings dialog '5' )
- Passkeys have to explicitly enabled in the browser plugin:

Regular Username / Password
- Take care that the KeePassXC icon on the top right is 'green' = connection to vault is active.
- Open the login page in the browser.
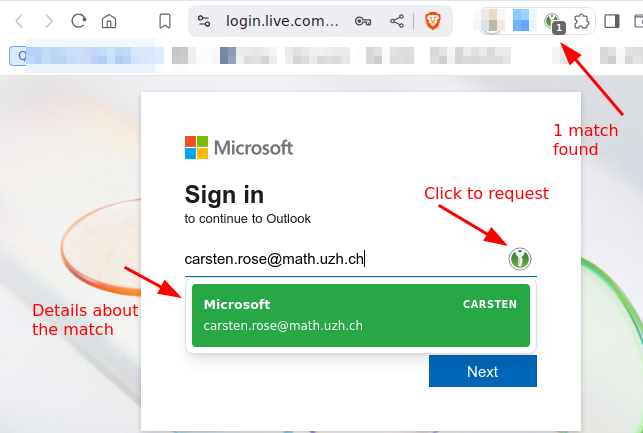
- Click on the small green kp icon.
- Choose the account.
MFA
TOTP
To use TOTP with Microsoft Office 365 login: Add another (than MS-Authenticator-) app, as second factor How To
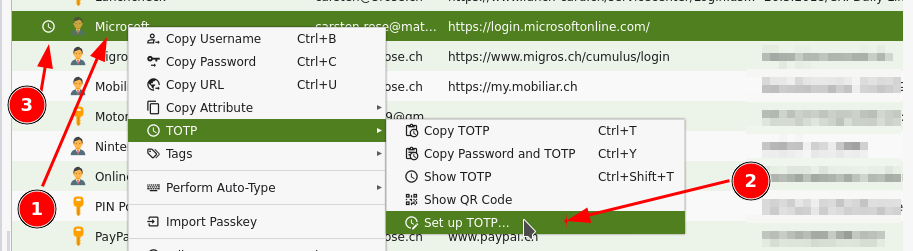
Add TOTP functionality to individual accounts: Account > right mouse click > TOTP > Setup TOTP
- On a MFA-TOTP secured login website, just login as usual with KeePassXC, on the next page, where the one time token is requested, click again on the green symbol.
Hint:
On the TOTP setup you have to provide the 'shared secret'.
- The shared scecret is provided by the website which hosts the login, typically where the MFA can be configured.
- Either in plaintext like 'ABCD EFGH 1234 IJKL 5678 MNOP QRST UV89'.
- As a QR code to scan.
Here sometimes it's a URL or a fido string.
- If it is not in plaintext in the URL, hopefully the assigned app (=keepassdx) opens.
- Option: be creative - scan the QR, look at the url (or send the URL via 'share' to yourself): you should see the shared secret as an argument in the URL.
Passkey
Passkey / webauthn are offered as an additional way to use MFA.
- Passkeys offers more security than TOTP and should be used when possible.
- But: Some websites work better than others. E.g. eduid.ch is ok, gitlab is ok but with popup, Microsoft is broken for Linux/Chrome/KeePassXC, ...
Recovery Keys
- Some services offers recovery keys.
- Copy the keys in corresponding account record in KeePassXC.
- If you used a key (it's burnt now), remove it from the list (if there was only one key, update it with the new one).
Same account / different URLs
Some services, especially Microsoft (https://login.live.com/, https://login.microsoftonline.com/), uses different URLs to login.
- Per account, add further URLs:
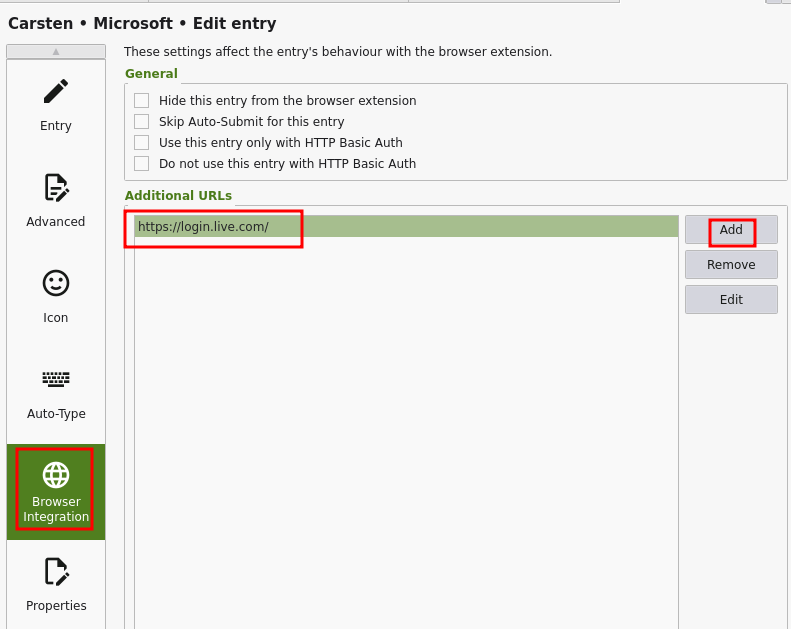
This is very powerful - add as many URLs you like to the same account record - the helps to keep your vault clean!
