- KeePassXC can be used from within a browser (Chrome, Chromium, Firefox, Vivaldi, Brave, ...)
- Browser connection to KeePassXC is nice: different browsers offer the same accounts/credentials - if synced via cloud than also on different computers.
- TOTP service (one time token).
- Passkeys support.
- Again, think on this: There is only one source of truth (=one KeePassXC vault), in all browsers you have all your credentials available.
Finally:
no more MS-Authenticator app needed
no more single device dependency (Phone at home, ...)
login to any MFA protected website without a mobile phone - Biggest advantage: your second token are controlled by you, not any provider.
still secure - the second factor is now your KeePassXC.
Settings
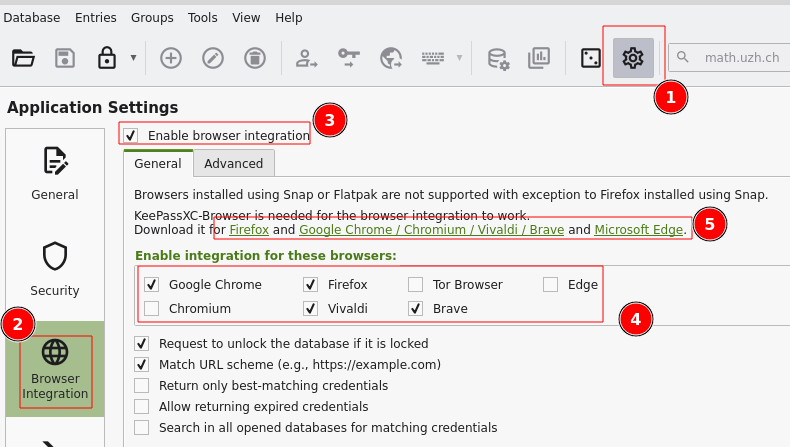
Settings > Browser Integration > Enable integration ...: Chrome, Firefox, ...
Browser Plugin
- Install the corresponding browser plugin (links to app store: check settings dialog '5' )
- Passkeys have to explicitly enabled in the browser plugin:

Regular Username / Password
- Take care that the KeePassXC icon on the top right is 'green' = connection to vault is active.
- Open the login page in the browser.
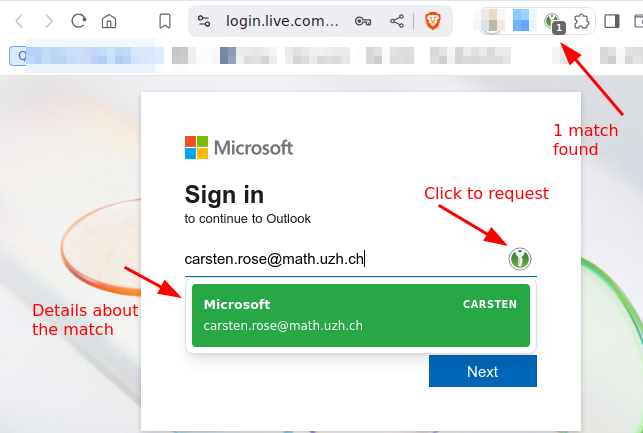
- Click on the small green kp icon.
- Choose the account.
MFA
TOTP
To use TOTP with Microsoft Office 365 login: Add another (than MS-Authenticator-) app, as second factor How To
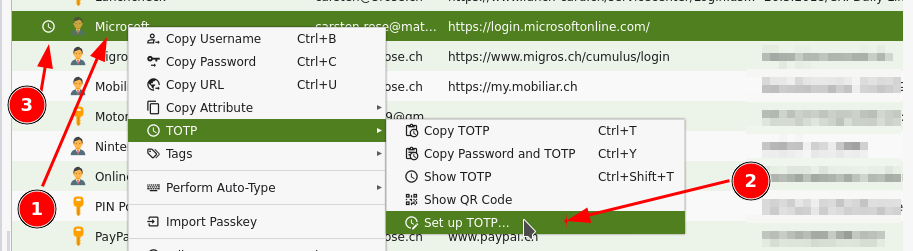
Add TOTP functionality to individual accounts: Account > right mouse click > TOTP > Setup TOTP
- On a MFA-TOTP secured login website, just login as usual with KeePassXC, on the next page, where the one time token is requested, click again on the green symbol.
Hint:
On the TOTP setup you have to provide the 'shared secret'.
- The shared scecret is provided by the website which hosts the login, typically where the MFA can be configured.
- Either in plaintext like 'ABCD EFGH 1234 IJKL 5678 MNOP QRST UV89'.
- As a QR code to scan.
Here sometimes it's a URL or a fido string.
- If it is not in plaintext in the URL, hopefully the assigned app (=keepassdx) opens.
- Option: be creative - scan the QR, look at the url (or send the URL via 'share' to yourself): you should see the shared secret as an argument in the URL.
Passkey
Passkey / webauthn are offered as an additional way to use MFA.
- Passkeys offers more security than TOTP and should be used when possible.
- But: Some websites work better than others. E.g. eduid.ch is ok, gitlab is ok but with popup, Microsoft is broken for Linux/Chrome/KeePassXC, ...
Recovery Keys
- Some services offers recovery keys.
- Copy the keys in corresponding account record in KeePassXC.
- If you used a key (it's burnt now), remove it from the list (if there was only one key, update it with the new one).
Same account / different URLs
Some services, especially Microsoft (https://login.live.com/, https://login.microsoftonline.com/), uses different URLs to login.
- Per account, add further URLs:
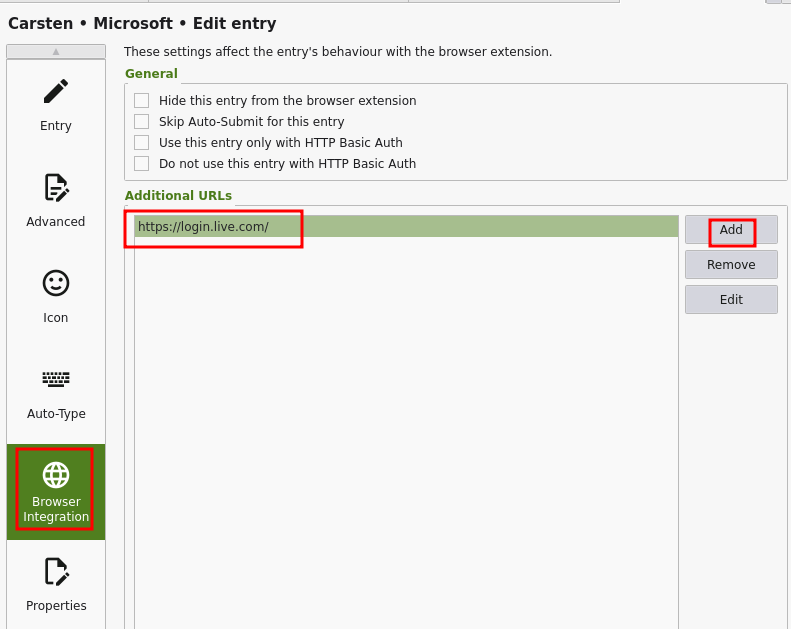
This is very powerful - add as many URLs you like to the same account record - the helps to keep your vault clean!